Three emerging threats: Climate change, vandalism and cyber-attack
E. MUNOZ, Dynamic Risk, Houston, Texas
Pipeline integrity management systems (PIMSs) are now common practice, driven by the Pipeline and Hazardous Materials Safety Administration (PHMSA) requirements in the U.S. In June 2022, the PHMSA updated an advisory bulletin on earth movement and geohazards to monitor changing weather patterns and consider the risk posed by climate change.1 In 2022—prompted by the Colonial Pipeline cyber-attack in 2021—the PHMSA began inspecting for and enforcing components of cybersecurity, mainly control room regulations, integrity management plan requirements and emergency plan regulations.2
This article discusses the threats associated with climate change, vandalism and cyber-attack from the perspective of existing risk models. Risk varies over time, and so does the effectiveness of prevention and mitigation measures. Risk assessment, an integral part of any PIMS, must evolve to address new treats prompted by:
- Extreme weather events (climate change)
- Increased computational capabilities and data availability (cyber-attack)
- Changes in behavioral patterns (vandalism)
- Enhanced mobility (vandalism)
- The complexity of cyber-physical networks (cyber-attack)
- Malevolent intent to disrupt the operation of critical infrastructure (vandalism).
Climate change. Extreme weather events have increased in the last decade. For example, the greater Houston, Texas (U.S.) area has experienced five once-in-a-lifetime events: three winter storms (2014, 2021 and 2022), a category 5 hurricane (2017) and the area’s first tornado (2022). The management of extreme weather events with the potential to impact oil and gas assets requires long-term regional predictions.
Climate scientists are aware that decision-makers require narrowing the uncertainty of future predictions. A review of temperature models has shown identical predictions in a 15-yr horizon but high variability beyond that, create a spread in results—the spread occurs in the number of years to reach a target increase on average temperature.3 The uncertainty in climate models arises from three factors: internal fluctuations of the system that might reverse for up to a decade the long-term trends of climate change; model uncertainty in response to radiative forcings—the balance between the radiative energy that enters the atmosphere and the amount of energy that leaves the atmosphere; and scenario uncertainty in the future, influencing factors such as greenhouse gas (GHG) emissions.
The importance of internal model variability increases at smaller spatial scales and shorter times scales. Proper initialization and validation of the model require adequate observational data, which is scarce. It is envisioned that real-time data feedback will eventually be used to adjust climate models. To paraphrase a recent update on the state of climate models: “Waiting for perfect information, as climate scientists are continually urged to do, means it will be too late to act […] sensible risk management addresses risk in time to prevent it happening, and the time is now.”4
Extreme weather events are herein defined as meteorological events with a 30% increased intensity and coverage from the maximum recorded event, in accordance with a Canadian advisory for future planning. Extreme weather events cannot be readily incorporated into existing risk models due to the high uncertainty of their likelihood, and the lack of meaningful lagging/leading indicators. The proposed climate change risk management framework, shown in FIG. 1, consists of speculative “What if?” scenarios of extreme weather events with an emphasis on consequence assessment.
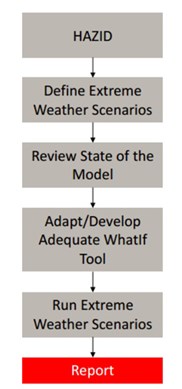
FIG. 1. Proposed framework for extreme weather events risk management.
Hazard identification (HAZID), or threat re-assessment, should be performed regularly to identify new or emerging threats. Engage all internal and external stakeholders in the discussion on the impact of climate change on the existing asset inventory and routine operations. Threat interactions should also be considered. Document the conclusions from the hazard/threat identification process for reference in the subsequent steps and for eventual review by the pertaining regulators.
When climate change has been identified as an active threat, the integrity team should define the extreme weather events to be modeled. TABLE 1 presents a non-exhaustive list of common extreme weather events to consider, dependent on the type of asset and location.
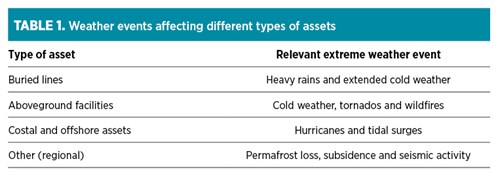
To expand on TABLE 1, seismic activity is not linked to climate change but should be modeled as an extreme event and should be considered in “double whammy” scenarios, simultaneous events or events in sequence. An example of a double whammy would be the California wildfires in late 2017 followed by high winds and heavy rains in early 2018 that resulted in mudslides and debris flow over the Montecito hillsides, leading to 22 deaths and a 2-wk period of gas service interruption to nearby communities.5
The third step of the framework in FIG. 1 reviews the risk model in place to ensure it has the adequate features to model extreme weather events. In the author’s experience, the following three features must be reviewed in pipeline risk models:
- Verify that the weather-related outside forces (WROF) assessment method is suited to model the effects of extreme weather events.
- Modify the consequence of failure (CoF) algorithm to represent the increased costs/times for remediation in the aftermath of an extreme weather event.
- Verify the incorrect operations (IO) assessment method can account for the increase in operation stress during an extreme weather event (e.g., wildfire incidents that affect operations rather than damage the asset).
At the end of the model review, the integrity team should be able to propose an implementation roadmap for the pertinent algorithm/tool modifications.
Following the risk model review, the fourth step is to review the “What if?” tool/module (if any) to ensure it can make a risk run with the inclusion of each severe weather event determined in the second step, focused on the group of assets or regions of interest.
The third and fourth steps of the framework involve iterative modifications to the risk model and “What if?” tools, and can take years to implement, depending on team resources and priorities. Once the required features are in place, the integrity management team should run extreme weather scenarios and report its findings. Climate change is an evolving threat that should not be reported on an annual basis. Its impact does not translate well in a corporate risk matrix.
The author’s company’s framework recommends a standalone report of the extreme weather events assessed with an emphasis on the increase in CoF provoked by the different scenarios considered. Communicate results to all internal and external stakeholders with pertinent subject matter expert (SME) workshops to determine a list of mitigation/remediation measures, the associated cost/benefit analysis, and an implementation timeline. The results of the “What if?” analysis can also be used in resilience plans to natural forces, like the one recently prepared by the Southern California Gas Company.6
Vandalism (security risk). The 2020 American Society of Mechanical Engineers (ASME) B31.8S Standard, “Managing system integrity of gas pipelines,” classifies vandalism as a threat under third-party damage, with data requirements listed in Appendix A along with the number of past incidents caused by vandalism. Depending on the definition, vandalism may include components of intentionality—the Cambridge dictionary defines vandalism as the crime of intentionally damaging property belonging to other people, while Merriam Webster defines it as the malicious destruction or defacement of public or private property. The framework proposed here aligns with the security risk guidelines issued by the U.S. Department of Transportation (DOT), the U.S. Transportation Security Administration (TSA) and the American Petroleum Institute (API), leading to the preferred term “security risk” to represent the different degrees of malicious threats (e.g., theft, vandalism, arson, sabotage, terrorism, armed conflict). Cyber-attack/cybersecurity threats are generally left out of the “physical” security (i.e., vandalism) risk framework.
The integrity team is generally not in charge of asset security. The asset security team, in turn, is generally unfamiliar with the concept of degradation risk, though they may use some indicators like crime indexes. The two relevant security guidelines in the U.S. have similar methods and the proposed unified risk-based method is shown in FIG. 2.7,8
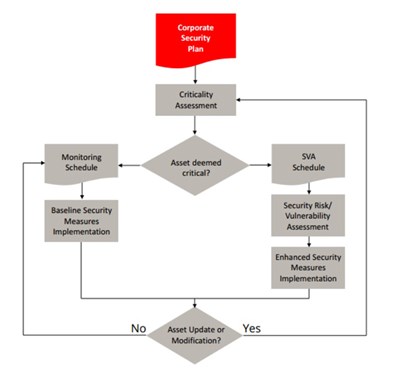
FIG. 2. Security risk-based method following TSA/API guidelines.
An effective corporate security plan should provide guidance for the following:
- Roles and responsibilities
- Inventory and hierarchy of assets to be assessed for security risk
- Data sources and data providers
- Criticality assessment method
- Security vulnerability assessment (SVA) method
- Corporate risk matrix
- Scheduling rules (monitoring and SVA)
- Baseline security measures implementation criteria
- Enhanced security measures implementation criteria.
It is inconvenient to perform an SVA and implement enhanced security measures on all physical assets since the inventory can be extensive and span different jurisdictions. Base any risk-based approach in a ranking system of the assets to help prioritize the in-depth assessment and the ensuing security risk reduction measures. Perform an initial asset categorization in a criticality assessment, which would ideally be a desk review in one session by the security team. A proposed criticality ranking is based on the following criteria:
- Critical asset designation by local regulators
- Asset loss financial value
- Asset attractiveness
- Criminal activity in the vicinity
- Presence of inside actors.
Regulators like the TSA or the Canada Energy Regulator (CER) have the power to designate a facility as a critical asset: those assets should be prioritized in the SVA schedule. Most pipeline risk models include a financial factor to represent material losses, service interruption, loss of personnel/human life, loss of reputation and environmental impact. Financial factors should also consider the impact on system redundancies, asset interdependencies and interruption of contracts in place.
Asset attractiveness is a factor that assesses the perceived value of the asset and has two components: potential consequence and target recognition. Asset attractiveness is an indication of the correct selection of the target, the likelihood of the attack, and the effect of any deterrence measures. A simple assessment method of target attractiveness would consider the following items: land use as an indicator of remoteness, service/utility as a classifier for perceived consequence, and lack of signage and fencing as a measure of lack of deterrence.
Criminal activity in the vicinity of an asset can be used to forecast opportunistic and premeditated attacks. Some property algorithms (e.g., CAP Index) have been developed to forecast attacks targeting specific types of businesses (retail, banking, utilities, government, hospitals, etc.) and can be easily incorporated into the criticality assessment.
Physical security risks distinguish between external and internal actors—both TSA and API guidelines recommend making a distinction between the nature of the adversary. In the author’s experience, internal actors can optimize the target selection, render any deterrence measures ineffective and elucidate walks around most physical measures. Past reviews by the author’s company of available security measures have found that procedural/system measures are effective to prevent attacks by inside actors. From the risk model perspective, the presence of inside actors should: maximize or invalidate the attractiveness factor, depending on the algorithm, since any target obfuscation and deterrence is ineffective; decrease the creditability of any physical measure factored into the asset vulnerability; and increase the likelihood of failure (LoF) until the insider is deactivated—an insider can jump directly to attack execution, skipping target recognition, surveillance, planning and rehearsal steps.
Developing indicators for the presence of inside actors is controversial since it implies having some type of intelligence on the operator’s own employees and contractors. A proposed (non-controversial) leading indicator of an insider’s presence would include factors such as the recent turnaround of employees and contractors, and the satisfaction level from any internal surveys.
The criticality assessment should produce a ranking of assets by criticality score. A threshold value of an asset’s criticality should be determined beforehand. Any critical asset should be scheduled for an SVA, with priority given to assets designated critical by the regulators. Non-critical (lower priority) assets should be monitored to assess the necessity of baseline security measures, such as fencing and signage.
An SVA should be performed on critical assets—this assessment can be adapted to be equivalent to a risk assessment. The SVA is an in-depth assessment, preferably onsite, that requires the participation of asset stakeholders. The purpose of the assessment is to determine risk as a function of the following factors:
- Active threats
- Asset attractiveness
- Asset vulnerability
- Actors/adversaries
- Financial consequences.
Financial consequences and target attractiveness consider the same factors specified by the criticality assessment and should be updated with any additional information the asset stakeholders might provide. Asset vulnerability is a measure of the effectiveness of the security measures in place and is generally assessed through a long questionnaire concerning the implementation of physical and technical measures, and security programs and procedures. The author’s company has reworked those questionnaires to match the measures/programs with the active threats and adversaries. For example, cursory vehicle identification and search help prevent theft and terrorism but are not necessarily effective against political demonstrations or arson.
The SVA results should be used as the basis for the implementation of enhanced security measures specific to the active threats and actors and hardening measures aimed at reducing the consequence of a potential attack. Criticality should be re-assessed when a major modification to the asset process occurs (i.e., asset upgrade/downgrade), when planned security or hardening measures are implemented, or at a pre-established re-assessment interval.
Cyber-attack (cybersecurity risk). Oil and gas processes and systems involve increased operational complexity (e.g., increased pressures/flows, more interdependencies, tighter combination between the computational systems and physical units). Constant technological innovation creates new cyber threats that create high initial uncertainty, so they are difficult to model quantitively. Oil and gas industry cyber-physical systems are deemed more complex—and so more prone to cyber-attacks—in the upstream and downstream sectors than in the midstream sector. For example, exploration and production (E&P) systems operate with relatively low cyber risks, but their operations will soon require real-time big data acquisition and processing in computing clusters that will, in turn, multiply cyber-attack effects. Big data can be defined as large sets of data collected by the operator that can be mined for information and used in predictive modeling. Legacy E&P assets with low cybersecurity considerations will magnify those cyber vulnerabilities during operation and abandonment. Finally, cyber risks at the top tier [information technology (IT) systems] and bottom tier (field technology systems) pose greater consequences in the upstream sector. In contrast, the midstream sector is, and will remain, a series of supervisory control and data acquisition (SCADA)-centric systems.
Cyber-attacks can either invade and control internal control systems (ICSs) seeking to compromise business continuity, or target sensitive data on business or enterprise networks that could impact current and future ventures. PIMSs are primarily concerned with attacks on ICSs. API Standard 11649 provides a framework for pipeline ICS cybersecurity risk management, which is an adaptation of the wider application framework published in NIST SP 800.37.10 The API framework kept all the elements of the NIST framework, as illustrated in FIG. 3.
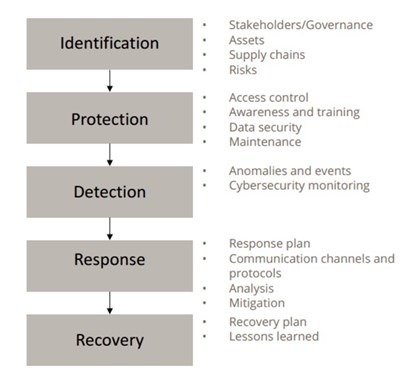
FIG. 3. Pipeline ICS cybersecurity risk management elements based on API STD 1164.9
Cyber threats risk assessment is similar to other threat risk models. LoF considers both threat-specific factors and system vulnerability. Common threat-specific factors to consider include:
- Skill required for the attack
- Opportunistic attack vs. persistent attack
- Actor/adversary.
The vulnerability of the system can be characterized by the following parameters:
- Discoverability
- Exploitability
- Awareness/confidentiality
- Detectability (i.e., logged/not logged user).
CoF should consider common business factors, such as financial and reputation loss, and additional technical factors such as data integrity loss, IGS availability loss, confidentiality loss and user accountability loss.
The API STD 1164 risk scoring, risk rating and impact severity levels are aligned with API STD 780. Therefore, the possibility exists to unify security and cybersecurity risk models.
Integration with existing pipeline risk models. Modeling emerging threats is challenged by the data and monitoring method availability. Initial risk models for these threats are, at best, index-based rankings suitable to prioritize mitigation measures, which might conflict with the maturity of other components of the pipeline risk model.
The effect of climate change cannot be incorporated in most risk models to generate annual predictions with the effects most effectively modeled as “What if?” scenarios to define response plans and resilience measures. The risk models for security and cybersecurity can be directly implemented into an existing risk model or their risk results can be incorporated as inputs.
Standalone models managed by SMEs external to the PIMS team tend to create data silos and incompatible data repositories. A protocol for stakeholder and tool management is recommended to make available all information relevant to PIMs decision-making.
Takeaways. The effects of climate change can be assessed by modeling extreme weather scenarios with a “What if?” tool. TSA guidance and API STD 780 provide a framework for security risk assessment, while API STD 1164 provides a framework for pipeline cybersecurity risk assessment. Both security and cybersecurity risk assessments can be integrated into an existing pipeline risk model, and will require the integration of new SME information, traditionally residing outside pipeline integrity departments.
LITERATURE CITED
1 U.S. Department of Transportation—Pipeline and Hazardous Materials Safety Administration (PHMSA), “Potential to damage to pipeline facilities caused by Earth movement and other geological hazards,” 2022, online: https://www.phmsa.dot.gov/regulations/federal-register-documents/2022-11791
2 U.S. Department of Transportation—Pipeline and Hazardous Materials Safety Administration (PHMSA), “Remarks of the Deputy Administrator Tristan Brown before the American Petroleum Institute Control Room and Cybernetics Conference,” May 3, 2022, online: https://www.phmsa.dot.gov/news/remarks-deputy-administrator-brown-before-american-petroleum-institute-cybernetics-conf
3 Hawkins, E. and R. Sutton, “The potential to narrow uncertainty in regional climate predictions,” Bulletin of the American Meteorological Society (BAMS), Vol. 90, Iss. 8, August 2009.
4 Spratt, D. and I. Dunlop, “What lies beneath: The understatement of existential climate risk,” BreakThrough, National Centre for Climate Restoration, Melbourne, Australia, 2018, online: https://climateextremes.org.au/wp-content/uploads/2018/08/What-Lies-Beneath-V3-LR-Blank5b15d.pdf
5 U.S. Federal Emergency Management Agency (FEMA), “California wildfires, flooding, mudflows and debris flows (DR-4353),” September 2018, online: https://www.fema.gov/disaster/4353
6 SoCalGas, “Case studies of multi-sectoral resilience to natural disasters,” ICF, August 2022, online: https://www.socalgas.com/1443742022576/SoCalGas-Case-Studies.pdf
7 U.S. Transportation Security Administration (TSA), “Pipeline security guidelines,” April 2021, online: https://www.tsa.gov/sites/default/files/pipeline_security_guidelines.pdf
8 American Petroleum Institute (ANSI/API) Standard 780, “Security risk assessment methodology for the petroleum and petrochemical industries,” 1st Ed., May 2013, online: https://www.api.org/~/media/files/publications/whats%20new/780%20e1%20pa.pdf
9 American Petroleum Institute (API) Standard 1164, “Pipeline control systems cybersecurity,” 3rd Ed., 2021.
10 National Institute of Standards and Technology (NIST) Special Publication (SP) 800-37, Rev. 2, “Risk management framework for information systems and organizations: A system lifecycle approach for security and privacy, 2018, online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-37r2.pdf
NOTE
This article was part of the proceedings of the 2023 Pipeline Pigging and Integrity Management Conference, and has been reproduced with permission from the copyright owners.
ABOUT THE AUTHOR
Eduardo Munoz is a Principal Consultant for Dynamic Risk and is a technical authority with 20 yr of experience in risk management and integrity assurance for onshore/offshore assets. In his current role, Munoz is responsible for the continuous improvement of risk models and provides specific project technical leadership in the areas of risk assessment, fitness-for-service, maximum allowable operating pressure (MAOP) reconfirmation, materials verification, crack management, digital solutions, data mining, security risk and failure investigation.




Comments